Manage every crisis simply and professionally.
Discover the comprehensive range of services offered by FACT24 – the integrated solution for proactive crisis management and emergency alerting in critical business situations.

Crises cannot be prevented,
but we can help you overcome them.
No matter what crisis situation impacts you: With the right digital crisis management software, you can better manage critical situations. We have developed FACT24 to make it easier for companies of all kinds to safeguard lives and assets.
Digital crisis management and emergency response with FACT24 Software-as-a-Solution is:
Proactive
Good crisis management begins before the crisis. With preventive measures, training and preparation as well as consistent monitoring of all incidents. FACT24 helps you to intervene as early as possible. In the best case scenario, before an incident turns into a crisis.
Reliable
We provide a dedicated and personal service on request 24/7, across 13 locations worldwide. We guarantee the availability of FACT24 – due to our resilient infrastructure, ISO certification with high regard to data protection and information security.
Simple
Critical situations can be complex to manage, therefore you need a solution that is simple to operate. FACT24 enables you to plot the entire BCM process chain in a single tool. So you can concentrate on what matters most during a critical event.

Integrated solution for proactive crisis management and emergency notification with FACT24
FACT24 Application Areas for
Emergency Notification and Crisis Management
With FACT24, you can design your crisis management proactively and digitally, from preparation to evaluation. It consists of two central applications: FACT24 ENS+ stands for Emergency Notification Services, FACT24 CIM allows for full crisis and incident management during critical events. Find out more about the areas of application that are covered:
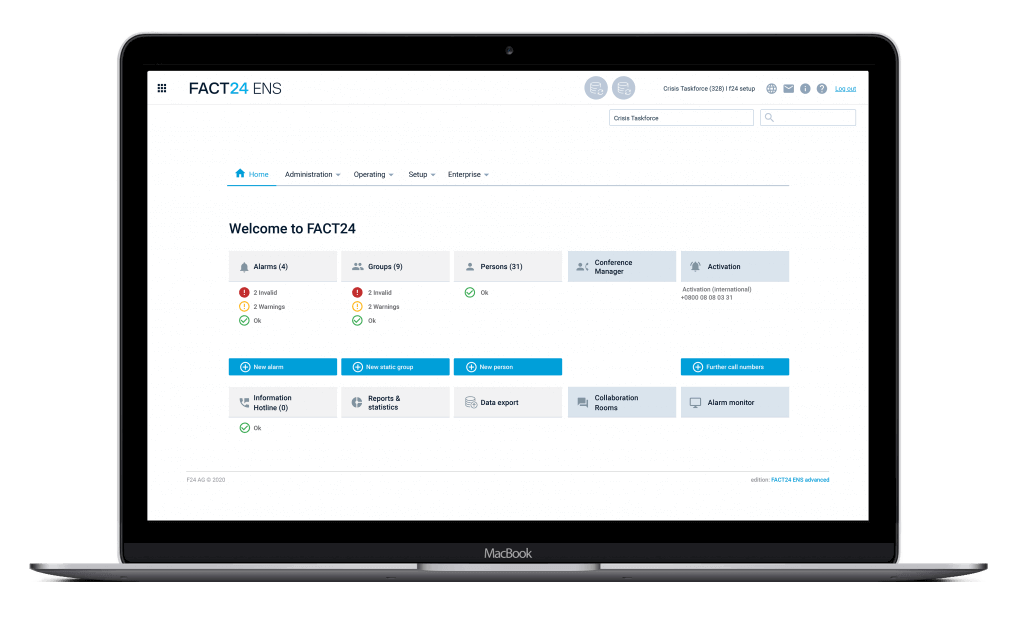
FACT24 ENS+
Secure and comprehensive Emergency Notification Services
Initiate relevant rescue measures, prepare them and analyse them afterwards to optimise your internal processes.
FACT24 can also be connected directly to sensors and technical equipment and automatically alert the emergency team in the event of an incident.
Alert the relevant teams or activate an evacuation if required immediately, to guarantee the safety of all those affected.
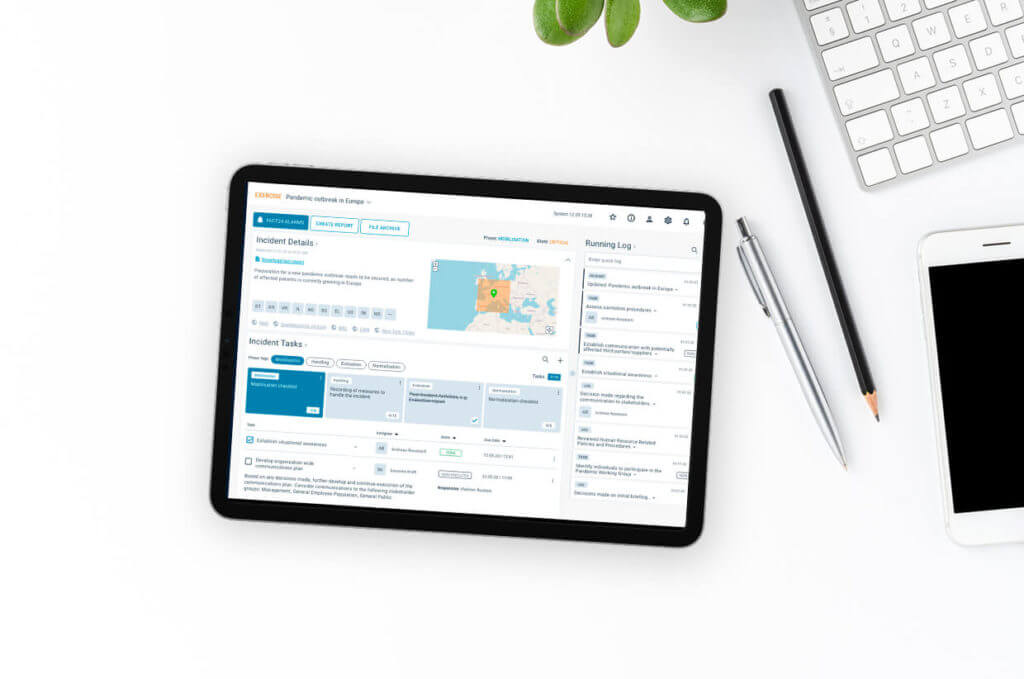
FACT24 CIM
Proactive 360° crisis management with FACT24 CIM
Observe all kinds of risks. Prepare today to be able to act tomorrow and avoid business or reputation damages.
For critical situations you need a solution that is simple to operate and can plot the entire BCM process chain in a single tool.
The all in one functionality is given due to the connection of our secure and comprehensive FACT24 ENS+ functionalities.
More than 5.500 Customers from All Industries
Trust the Services of F24 in Critical Situations.